
It has never been easier to connect and share stories, experiences and ideas with people across the world. Our capacity to be almost constantly online is unprecedented and it has a profoundly positive effect on our lives. However, as it gets easier to get and stay connected, there are new risks to your personal data security. You can’t sit back and assume everything online is safe and secure. Take the wheel, and steer towards better cyber-security.
This video that Norton Security created with the help of Geek Squad offers some insights on the importance of Cybersafety:
Here are some helpful rules we all need to follow:
The First Rule: Be Alert, Aware and Informed
The first critical step for protecting yourself online is acknowledging the vulnerabilities and risks involved. Most successful cyber-attacks on individuals aren’t the result of intrusive malicious programs forcing their way into your data storage. It’s the misleading email, the deceptive Facebook post, or the telephone call from someone pretending to be tech support that has the most danger. This method of hacking is called social engineering, and it is incredibly successful. Fortunately, you can protect yourself with a few simple preparations:
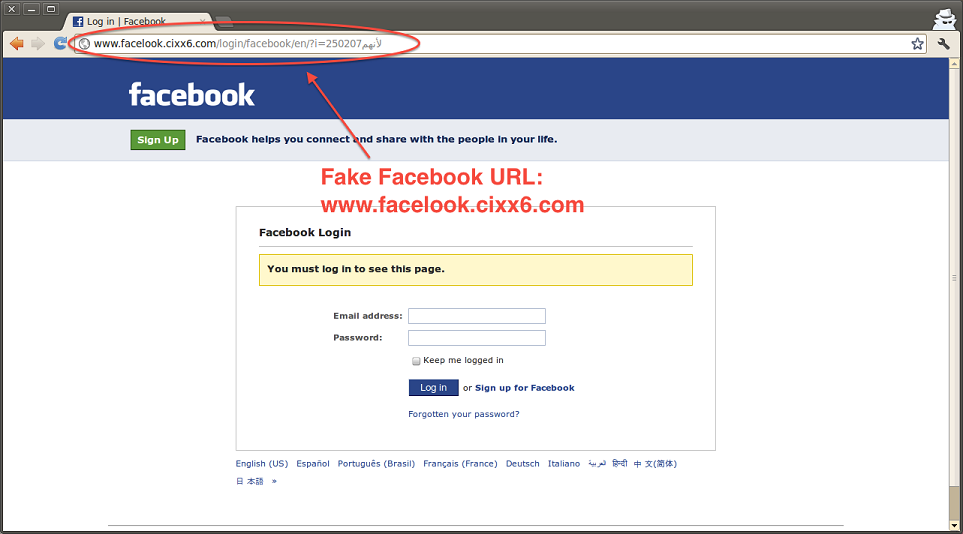
1) Look Closely: Remember that no reputable company will contact you and ask you to change your password or enter your account information. Online scammers will use website addresses that are similar to the legitimate ones, so look very closely at the link they want you to use. If you hover over a website address link in your email, the actual destination link will show up in a text box. If the address looks wrong, don’t go there.
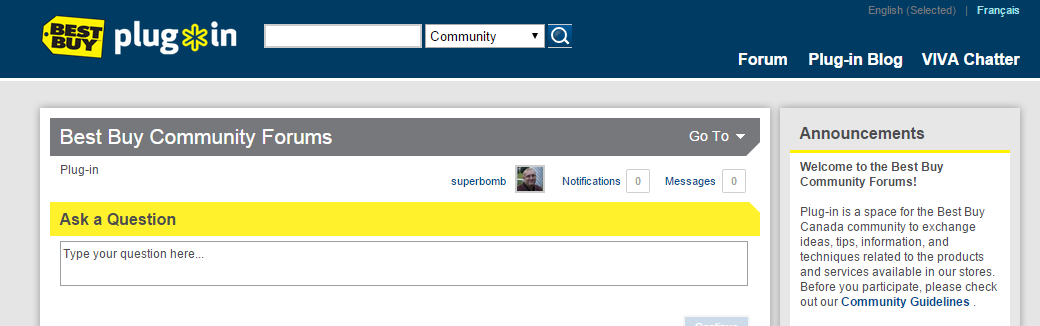 2) Use the wisdom of crowds.Your fellow Plug-in netizens have seen and experienced these scams before and they are happy to share that information. A quick post to the thousands of informed Canadians on the Plug-in community forum asking for information can bring a wealth of useful help. And it never hurts to do a little Google fact-checking as well.
2) Use the wisdom of crowds.Your fellow Plug-in netizens have seen and experienced these scams before and they are happy to share that information. A quick post to the thousands of informed Canadians on the Plug-in community forum asking for information can bring a wealth of useful help. And it never hurts to do a little Google fact-checking as well.
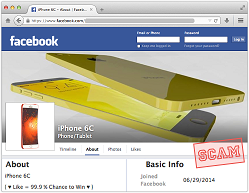
3) There’s no such thing as a free lunch. Promotional offers and giveaways can be completely aboveboard. It’s a way for a company to raise awareness of their product, attract potential customers, and gather information. But if there’s no connection to the company’s product offering, then their goal may be to harvest that information for illegitimate use. Before you click on a “free phone” offer on Facebook, take a closer and more critical look.
The Second Rule: Your password is your Key
The temptation to simplify your life by using one password for every site is strong. We’ve all felt it. But it’s a terrible blow to your cyber-security to give in to that temptation. Using the same password at every site you visit means you are trusting your entire digital life to whichever site has the weakest security. As the old saying goes, “the chain is only as strong as its weakest link”. Being fully secure means having a different password for every site. At the very least, you must use strong, unique passwords for your most important online activities: email, banking, and accessing government services.
And how do you make a strong password? The length of the password is a key factor. For each additional character you add to the password, you increase the difficulty of cracking or guessing it exponentially. Most sites will require you to use a mix of letters (upper and lower case), numbers, and special characters. If they don’t, you can build a password out of a more easily remembered phrase. Make sure the phrase is long and not easily guessed, like “monkeycheesehatpatio.” Neither human nor machine hacker will quickly guess that password. Whatever method you use to create your password, management will be the key to maintaining their efficacy. Set up a yearly schedule to change your primary passwords, keep your password list in a secure location away from your computer, and change any password at the first sign of suspicious interaction.
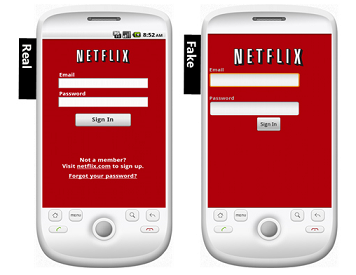
The Third Rule: Watch your security across devices
Your online interactions aren’t limited to what you do on your computer. Your tablet and your cellphone are also a part of your network, and you have to protect them as well. Malicious apps are as much of a threat as harmful PC programs, so be alert and research an app before installing it. Watch out for lookalike apps that try to misdirect you from the legitimate app to their own knockoff.
The Fourth Rule: Watch your network
Another element of cyber-security that needs to be considered is the network you connect to. For your home network, make sure that you have changed the administrator account password and that you’ve set your network to secure. An open Wi-Fi network is an invitation to misuse.
Speaking of open networks, let’s talk about those handy free networks offered by various restaurants and businesses. They are configured to be simple to use and connect to, which means their security is low. Sitting in the coffee shop and doing your online banking while sipping a cappuccino is not the best way to stay secure: Save the important stuff for a secure network or if always being connected is a necessity, consider using VPN (Ted Kritsonis wrote a great article on setting up a VPN here).
The Fifth Rule: Safeguard your important files
One type of online scam involves gaining access to your computer and then threatening to delete all of your data if you don’t pay up. The digital extortion scheme depends on the victim (you) having only one copy of their important files. It’s another strong argument in favour of having a second copy of all your data. With the various cloud storage services available (iCloud, Dropbox, Onedrive), you should be able to find a solution that will hold a safe second copy of your critical files. Keeping that data up to date will be up to you.
The Sixth Rule: Keep it all organized
The reality is that maintaining your cyber-security measures takes a fair bit of work and involvement. Upkeep is your next point of vulnerability. It’s easy to set everything up and make a vow to continue being vigilant, but life gets busy and maintenance gets ignored. This is why it’s a good idea to consider an internet security package. As an example, the Norton Security package covers multiple devices (5 for the deluxe package, 10 for the premium) and offers protection and support across operating systems and device types. The subscription also gives you unlimited phone support from Norton technicians, password management, and the ability to remotely erase a stolen or lost tablet/smart phone. The premium package also includes a family web content filter, and an online data backup service.
Want to learn more about Cyber Safety? Check out these recent Plug-In blog articles:
Cyber safety tips for you and your smartphone
Teach your kids about cyber safety
And be sure to ask Geek Squad too: they have in store and even in home service options
images from Sophos.com, eff.org, security-faqs.com, cbsi.com





Bad article. There are three rules in computer security.
1. do not own a computer
2. do not power it on
3. do not use it
Nothing can really fully protect you after that.
Going for the ironic angle are we?
No one can be 100% protected while on a PC, but these are some fantastic tips to help mitigate the threat. So I disagree with your assessment, this is a great article!
JB
I agree, very great article
PCs are part of our daily life and online access has become a key part of that experience. The way to play it safe is to take advantage of information like this post that point out the pitfalls and provide answers about how to defend against them—along with the feedback from people who have encountered various threats and schemes. As JB says (and thanks for the encouraging comments, BTW!), mitigate the threat. Knowledge is power …
Thanks for the positive comments, Drax86 and Juice0904. It’s true that there’s no 100% foolproof way to protect your computer, but that’s life. Risk mitigation and good security practices are the way to go.
Comments are closed.