 A malicious computer bug called WannaCry is spreading around the globe and you need to protect your PC now to ensure your machine stays safe. The criminals who released this menace on the internet intend to hold the information on your computer hostage until they are paid a sum of money: hence the infection has been called “ransomware.” You can protect yourself by going to the Microsoft website and downloading a security patch. You can also visit your local Best Buy and ask Geek Squad for a free Ransomware Vulnerability Assessment. They’ll determine if your PC is vulnerable to infection and needs an update. A Geek Squad agent will even show you how to run a Windows update yourself, at no cost.
A malicious computer bug called WannaCry is spreading around the globe and you need to protect your PC now to ensure your machine stays safe. The criminals who released this menace on the internet intend to hold the information on your computer hostage until they are paid a sum of money: hence the infection has been called “ransomware.” You can protect yourself by going to the Microsoft website and downloading a security patch. You can also visit your local Best Buy and ask Geek Squad for a free Ransomware Vulnerability Assessment. They’ll determine if your PC is vulnerable to infection and needs an update. A Geek Squad agent will even show you how to run a Windows update yourself, at no cost.
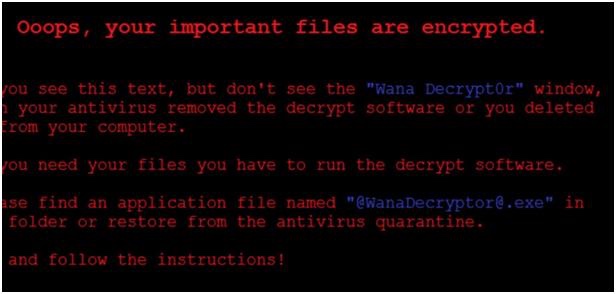
What is WannaCry, why is it so dangerous and what steps should you take to make certain your computer is safe?
Here’s everything you need to know:
|
FAQ What’s going on? How would I know it’s happening to me? How do I avoid this attack? What else can I do? If I’m affected and do not have my data backed up in the cloud or on an external hard drive, what can I do? If I’m affected and do have my data backed up, what can I do? You can also seek the assistance of our expert Geek Squad agents. You can come into the store for help, or we can come to your home or help you over the phone. If my computer is infected, how do I avoid it infecting other computers on my network? Click here for more information about Geek Squad Services. |
WannaCry is Ransomware
WannaCry is a very nasty form of malware known as Ransomware. Where traditional computer viruses are dangerous, they usually leave your computer still able to function when infected. In fact most rely on your PC remaining functional so they can lurk in the background logging keystrokes, capturing account data, looking for credit card numbers and similar actions. These are serious problems, but at least you can run security software.
Ransomware takes a different approach. Instead of leveraging your PC as a gateway to stealing your personal information or randomly destroy a few files, it encrypts your storage, effectively rendering the PC completely useless. You can’t boot the PC to run security software and you can’t access any of your data. The only out is to pay a ransom to the cyber criminals behind the attack, usually in Bitcoin. In the case of WannaCry, unlocking an infected PC requires forking over roughly $300 U.S. worth of Bitcoins—or over $400 Canadian. If the ransom isn’t paid quickly, the amount demanded increases …
Because trying to decrypt a PC without the encryption key is virtually impossible, authorities usually end up recommending affected users either pay the ransom or accept the loss of their information and reset their computer to factory settings.
WannaCry is Different From Other Ransomware
As if ransomware wasn’t already bad enough, WannaCry takes it to a new level. At this point, researchers believe it is based on an exploit created by the U.S. National Security Administration (NSA) called ETERNALBLUE. So, it’s government-strength malware that’s gotten into the wild. And it takes advantage of a Windows file sharing vulnerability so once WannaCry infects one PC on a network, it seeks out and infects others—no need for phishing to try to trick a human into downloading it.
How Did it Infect PCs In the First Place?
It’s believed that WannaCry first began attacking PCs through e-mail attachments. Unsuspecting users opened the attachments, infecting their own PC. It then spread through networks using that file sharing vulnerability.
A Lucky Break + Microsoft Steps In
We caught a lucky break when a security researcher examined WannaCry code and noticed it makes a call to a strange-looking domain name. That domain was unregistered, he registered it himself and this effectively acted as a kill switch that has stopped the network propagation.
Microsoft had already released security updates that patched the wile sharing vulnerability in the latest versions of Windows a month ago. However, Windows XP—which is no longer supported—was not patched. WannaCry was infecting PCs running older versions of Windows, and computers where someone had turned off security updates. The company took the unusual measure of releasing a security patch for Windows XP and Windows 8 that shuts down the vulnerability.
How to Protect Yourself From the Next WannaCry
It looks as though the worst is over from the initial WannaCry attack. Fortunately, most of the computers that were affected were running Windows XP and the combination of that kill switch, Windows patches and heightened vigilance have combined to slow it.
However, one of the nasty things about malware is that it has a tendency to mutate and come back. In the case of something that was as successful as WannaCry, it’s inevitable that criminal elements are already hard at work on the next variation. So how do you protect yourself and your PC from becoming a victim of WannaCry, the next big ransomware attack or any other computer malware?
 Keep Your Operating System Up to Date
Keep Your Operating System Up to Date
Your first line of defence is keeping your computer’s operating system up to date. Whether its Windows or macOS, keep up to date. Microsoft and Apple incorporate critical fixes in their OS updates and sometimes push out specific security updates. WannaCry was the perfect example of how falling behind and running an outdated operating system can leave your system vulnerable.
Be Careful Online
Many security experts will point out that the weakest link in computer security is us. The people using the PCs. Virtually every malware attack starts with criminals sending phishing e-mails. They direct you to a fake (but official looking) website to trick you into entering critical information. Or the e-mail contains an attachment that when downloaded, infects your computer. That’s suspected to be the method WannaCry used.
When using your computer (or any connected device for that matter), you need to be vigilant. Be extremely wary of attachments, especially when the e-mail sender isn’t known. Even if you know the sender, watch to see if the actual e-mail subject and text sounds like a “cut and paste” generic message instead of something personalized—some malware e-mails itself to everyone on an infected PC’s contact list. Beware of generic messages from legitimate-looking sources. Your bank won’t ask you to log into your account with a “Dear customer” e-mail. Found a USB flash drive on the floor? Be wary about plugging it in to your PC as some malware arrives on thumb drives that are casually left lying around to be found.
 Use Security Software
Use Security Software
It’s not a perfect solution, but installing security software and regularly scanning your PC will definitely minimize your risk of being infected by malware.
Back up Your Computer to an External Hard Drive
The closest you can get to bullet-proof protection from Ransomware like WannaCry is to do a complete backup of your PC to an external drive. Don’t just back up your data, don’t back it up to a partition on your PC’s storage and don’t leave the external drive connected when not in use.
If your PC is encrypted by WannaCry or another ransomware variation, this solution lets you escape without paying and in only a few hours. You boot your PC from a recovery disk, wipe it down, then do a complete recovery from the external drive. This gets your computer back to the state it was in when you last backed up—and with no encryption.

Want to learn more about computer security and spotting phishing e-mails? Check out this post I wrote last year.
WannaCry was a wake up call for how fast ransomware can spread and the seriousness of the repercussions. You probably weren’t directly affected this time, but it should serve as a warning to be prepared. If you have any doubts about security software and a backup strategy, GeekSquad can help you out with professional in store setup. If you’re still using an old Windows XP computer, WannaCry should help make the case that it’s time to consider upgrading to a new Windows 10 PC. And don’t forget, if you have any concerns about your computer’s vulnerability to WannaCry and ransomware, you can bring it to Geek Squad at any Best Buy location for a free Ransomware Vulnerability Assessment and no-charge assistance with updating Windows.



